Hi guys , I'm back again with a little nugget of wisdom, talking today about Azure App Proxy.
For those of you not familiar with it, Azure Application Proxy provides secure remote access to on-premises web applications if you have single sign-on with Azure AD.So basically this removes the need for a vpn client making your on-premise applications available on the go.Pretty cool stuff, I would say.
You can find comprehensive documentation and guides here: https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/application-proxy
As a proof of concept, my team and I played around with a couple of apps , some using forms-based authentication, some using windows-integrated and there is a tiny gotcha for IIS-based apps in order to get them working, which I'll mention later on in this article.
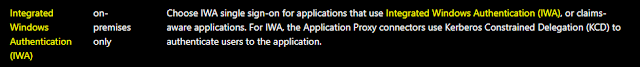
So looking at Single Sign-on options after you go through App registration and follow the steps in the MS guidelines you will want to go for WIA.
This will work just fine and it's quite easy to set up:
You basically start by following all the steps in this article:
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/application-proxy-configure-single-sign-on-with-kcd
TL;DR version as follows:
1.Install and configure your connector server(s).Very important: set up SPNEGO
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/application-proxy-connectors
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/application-proxy-connector-groups
https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-register-app
3.Go to your web app server on-prem and create an SPN with setspn -U -A HTTP/servername DOMAIN\service_account_name.Make sure the app pool runs under the service_account_name owning the SPN.
4.Go to your AD Users and Computers console, select your connector servers, go to the delegation tab, allow for any delegation method and add the SPN created at step 3.
5. In Azure AD go to Enterprise Applications - Select your registered app and add the Internal Application SPN and the delegated Login Identity:
6. Test the app and connect to it via SSO after the Azure MFA login.If it doesn't work and you get Access Forbidden in your browser you may see this in the event viewer of your on-premises Application Proxy Connector server:
If this is the case you may want to add Negociate: Kerberos as an Authentication Provider in IIS for that particular app pool.In my case it was failing as the only enabled provider was NTLM and it obviously didn't handle Kerberos requests very well.:
And if it still fails please go to your App pool - Configuration editor --> system.webServer --> security --> authentication --> basicAuthentication - defaultLogonDomain: True
Have fun!
For those of you not familiar with it, Azure Application Proxy provides secure remote access to on-premises web applications if you have single sign-on with Azure AD.So basically this removes the need for a vpn client making your on-premise applications available on the go.Pretty cool stuff, I would say.
You can find comprehensive documentation and guides here: https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/application-proxy
As a proof of concept, my team and I played around with a couple of apps , some using forms-based authentication, some using windows-integrated and there is a tiny gotcha for IIS-based apps in order to get them working, which I'll mention later on in this article.
So looking at Single Sign-on options after you go through App registration and follow the steps in the MS guidelines you will want to go for WIA.
This will work just fine and it's quite easy to set up:
You basically start by following all the steps in this article:
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/application-proxy-configure-single-sign-on-with-kcd
TL;DR version as follows:
1.Install and configure your connector server(s).Very important: set up SPNEGO
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/application-proxy-connectors
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/application-proxy-connector-groups
REG ADD "HKLM\SOFTWARE\Microsoft\Microsoft AAD App Proxy Connector"
/v UseSpnegoAuthentication /t REG_DWORD /d 1net stop WAPCSvc & net start WAPCSvc
2.Register your application(s):https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-register-app
3.Go to your web app server on-prem and create an SPN with setspn -U -A HTTP/servername DOMAIN\service_account_name.Make sure the app pool runs under the service_account_name owning the SPN.
4.Go to your AD Users and Computers console, select your connector servers, go to the delegation tab, allow for any delegation method and add the SPN created at step 3.
5. In Azure AD go to Enterprise Applications - Select your registered app and add the Internal Application SPN and the delegated Login Identity:
6. Test the app and connect to it via SSO after the Azure MFA login.If it doesn't work and you get Access Forbidden in your browser you may see this in the event viewer of your on-premises Application Proxy Connector server:
If this is the case you may want to add Negociate: Kerberos as an Authentication Provider in IIS for that particular app pool.In my case it was failing as the only enabled provider was NTLM and it obviously didn't handle Kerberos requests very well.:
And if it still fails please go to your App pool - Configuration editor --> system.webServer --> security --> authentication --> basicAuthentication - defaultLogonDomain: True
Have fun!